The risk management process as defined in ISO 31000 is presented below:
Establishing the context of a project is an important first step to any risk analysis. Without establishing the context in which the risks are to be framed,
it is impossible to determine the significance of any given uncertain event. Establishing the Context consists of 5 main components:
It is important to gather and specify key project information such as project name and description, key dates and budgets, as this provides crucial insight into the context of the risks that may follow. It is impossible to complete the sections that follow without at least a basic understanding of this information.
If available, the “Project Execution Plan” (PEP, sometimes called the Project Management Plan) is usually a good source of this data.
It is also important to note the key stakeholders involved in the project, as this can also influence other aspects of the context settings, especially the Project Significance.
The significance of the project to the stakeholder conducting the risk management process is dependent on both the magnitude of the investment (in terms of time and money) and the expected returns of the project, relative to the monetary capital of the stakeholder or the significance of the project to the strategic goals of the stakeholder. What one company considers to be a small investment could be “make or break” for another. Project significance can also extend beyond cost and schedule to reputation, environmental, or other types of significance.
Project significance guides the level of effort to be invested in risk management by the stakeholder, as risk management, like quality management, can devour as much of the stakeholder’s resources and capital as the stakeholder is prepared to invest. The higher the significance of the project, the more the stakeholder can justify investing in risk management.
The key reason for defining the project goals is that risks only apply to a project if they threaten or enhance the project goals. If the goals have not been defined, there would be doubt on whether a risk is relevant.
Is the aim to establish the project for:
• Maximum operating efficiency?
• For minimum environmental impact?
A goal can be anything provided it applies to the project.
For risk management, it is also important to identify and agree on the approach that is to be taken to risk management. This includes the frequency with which the Risk Identification, Risk Analysis, Risk Evaluation, & Risk Treatment cycle is to be performed or reviewed. Whether a qualitative and/or quantitative analysis approach is to be used at each major phase boundary of the project is also of importance as this establishes a plan and affects the budget for execution of risk management services.
For mature projects organisations, a further consideration when reviewing risk management performance is to evaluate the risk management performance to date. This helps to identify the strengths and weaknesses of what has been done to date, and whether it has helped to identify and treat risks that might have otherwise affected the project’s objectives. If the risk management performance to date has been poor, alternative risk management approaches and strategies need to be examined to improve this.
Risk identification is the first of three steps in the ISO 31000 Risk Management Process that comes under the heading of Risk Assessment.
Risk identification refers to the “process of finding, recognizing, and describing risks” (ISO 31000). For safety risks, this may refer to formal processes like hazard reports or scheduled inspections. However, for schedule and cost risks and uncertainties, processes such as workshops, interviews, or historical data sets are more commonly used. The relative benefits of these different approaches are discussed in the section that follows.
There are many ways to gather risk data, and some are more suited to some situations than others. Ultimately, there is no “right answer” as to which is best, but risk managers / analysts should be aware of the alternatives available and choose the best combination for the project and the risk management context identified.
• Historical Data – Where available, historical data is almost always the best resource to use as the input to an analysis, as it bypasses the potential influence of individual risk attitudes. If performing a quantitative analysis in a sophisticated analytical tool, actual historical data can be incorporated into models (along with trend information for future projections) using custom probability density distributions. This provides the most unbiased basis for identification of uncertainty trends, but is complicated and time consuming to prepare. An example of where use of historical data may be appropriate is in the modelling of a project where the price of fuel will be a determinant of project economic success.
• Interviews – Conducting interviews to gather risk information involves identifying key personnel within a project team and spending time with them individually to assess their attitudes towards different sources of uncertainty in the project. After all participants have been interviewed, the results for each source of uncertainty are collated and averaged to arrive at a final position for inclusion in the risk database or model. Interviews that are conducted so that the results are anonymous are especially effective in reducing the effect of senior management pressures to “toe the company line” which can sometimes cause people to provide overly optimistic responses to risk questions. However, interview processes usually take an extended time, and interviewees may have different frames of reference and biases when providing opinions on sources of project uncertainty that necessitate further time to reconcile conflicting opinions.
• Workshops – Workshops are useful in that they provide a quick and straightforward means of arriving at consensus views on sources of uncertainty within a project. They have the added benefit of ensuring a common frame of reference for all persons involved when expressing attitudes towards the uncertainties discussed. However, workshops require careful and experienced facilitation to ensure that some voices and opinions do not become dominant and others are forced to “fall into line” or are not heard. Further, organizing all the necessary (usually quite senior) stakeholders to be available at the same time can prove difficult.
For information on the what data should be gathered as part of best practice processes for risk identification, please refer to the section on Risk Properties
The following are some general techniques for the identification of risks. Each has their own benefits and limitations:
 • Brainstorming – A simple technique whereby stakeholders are asked to identify risks to the project based on their own perceptions or experience. This type of exercise is unstructured and particularly useful for identifying risks that might fall outside of traditional risk breakdown structures. If combined with use of “Post-its” on a board, groups can build up clusters of similar risks to indicate perceived importance and risks on which to focus (see also Risk Breakdown Structures and Checklists below).
• Brainstorming – A simple technique whereby stakeholders are asked to identify risks to the project based on their own perceptions or experience. This type of exercise is unstructured and particularly useful for identifying risks that might fall outside of traditional risk breakdown structures. If combined with use of “Post-its” on a board, groups can build up clusters of similar risks to indicate perceived importance and risks on which to focus (see also Risk Breakdown Structures and Checklists below).
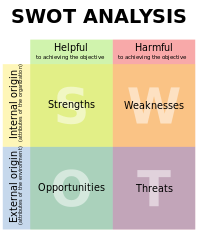
• SWOT Analysis – SWOT, as it applies to risk analysis is a structured risk identification process whereby stakeholders are asked to identify the strengths & weaknesses (internal factors) and opportunities & threats (external factors) of a particular project or process.
SWOT analysis tends to follow the same general processes as brainstorming, but overlays the structure of the 4 quadrant approach to assist in the identification process. Unlike other techniques, SWOT analysis is particularly useful for helping in the process of identifying positive risks (opportunities).
• Assumptions Analysis – The principal behind assumptions analysis is that every assumption actually represents a potential risk to the project. By challenging every assumption we’ve made to ask “what if it’s wrong?” we can identify new sources of risk.
• Risk Breakdown Structures and Checklists – An RBS is another example of a structured approach to brainstorming that can help in the risk identification process. By first identifying classes of uncertainty on a project (eg. Procurement uncertainty, weather uncertainty, etc.) we are provided with a prompting for the different potential sources of risk. Organisations typically develop an RBS for recurring types of projects against which risks are identified in order to ensure that the risk identification process always covers all the known potential sources of risk.
• Specific Opportunity Identification Sessions – Experience has shown, notwithstanding the benefit of SWOT analysis, that opportunities are difficult for groups to identify when also identifying threats. The tendency is for threat identification to dominate. It can be especially beneficial, rather like value engineering, to run special Opportunity identification sessions, whether guided by an RBS or alternative systematic approach, to identify Opportunities and how to enhance them through treatments.

